What Are Team Roles?
Team roles in Vast.ai’s platform are designed to streamline collaboration and enhance security by assigning specific permissions and access levels to different members of a team. These roles determine what actions a team member can perform and what data they can access within the team’s shared workspace/context.Types of Team Roles
- Default Roles: These are the standard roles with preset permissions, suitable for common team structures:
- Owner: Full access to all team resources, settings, and member management.
- Manager: All permissions of Team Owner apart from Team Deletion.
- Member: Has ability to view, create, and interact with instances, but no access to billing info, team management, autoscaler, machines, etc.
- Custom Roles: Custom roles allow team managers to create roles with custom, tailored permissions via permission groups. This feature is particularly useful for teams with unique workflow requirements or specific security protocols.
Creating Custom Roles
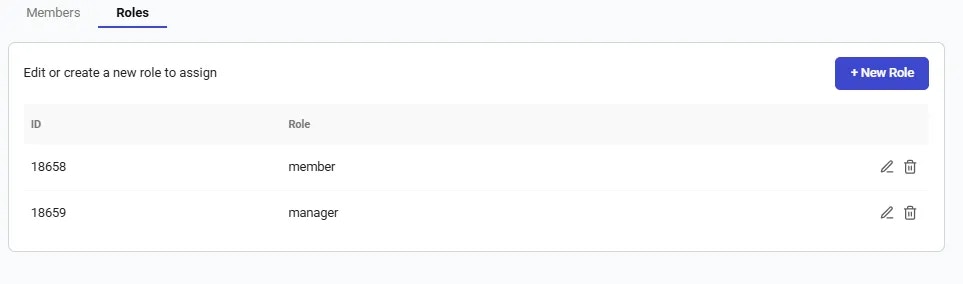
- Accessing Role Management: Custom roles can be created and managed through the Roles tab of the Members Page on the Vast.ai platform.
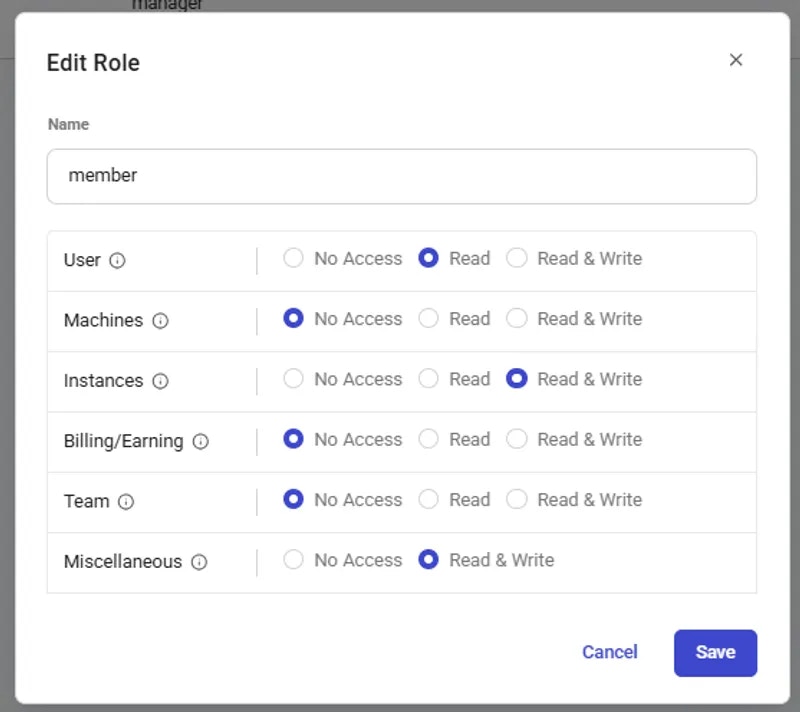
- Defining Permissions: When creating a custom role, you can select from a wide range of read/write permissions, such as instance creation, billing access, etc. This allows for precise control over what each role can and cannot do.
- Assigning Custom Roles: Once a custom role is created, it can be assigned to team members through the team management interface.
Default Roles
Edit Role
Role Syntax
All team roles are created through the team dashboard using the role editor. You can also create roles through the Vast CLI by passing in a permissions JSON object that delegates what group of endpoints can be accessed. Currently, the system only supports groups of endpoint categories, but soon it will be extended for further granularity. The current activated scopes are as follows- misc: Supports uncategorized operations like search offers, getting logs from various sources, etc
- user_read: Allows the usage of obtaining basic user data like email, credits, etc. Essential for web usage.
- user_write: Allows the ability to change account settings such as email, password, 2FA, etc.
- instance_read: Grants ability to view instances, and certain read-only instance operations
- instance_write: Grants access to instances and all relevant operations such as starting/stopping instances, cloud copy, reserving credits, etc
- billing_read: Ability to view billing page and get billing information
- billing_write: Ability to change billing page information
- machine_read: Read access to machines owned by the team
- machine_write: Ability to add/remove machines, and also edit machine settings
Text
Best Practices for Using Team Roles
- Clear Role Definitions: Clearly define the responsibilities and permissions for each role to avoid confusion and ensure effective collaboration.
- Use Custom Roles Judiciously: Create custom roles when predefined roles do not meet your specific needs. Be mindful of the permissions assigned to ensure team security and efficiency.